Hacking and its proponents have been in the forefront lately, what with hacking “groups” being more active and aggressive in their activities. The general public probably does not have an accurate idea as to what hacking really entails and what hackers really are like. Then again, I think that I am correct to assume that you know a tad more than your average joe. You might even have an experience or two to back you up. If this is the case, then you will definitely be interested in finding out just what kind of hacker you are. (Using the term rather loosely, I know.)
Well, wonder no more as the guys at IEEE Spectrum ((Source)) have done their utmost best to provide the only hacking chart you’ll ever need. That is, a hacking chart that will help you determine whether you are involved in activities that are good, bad, or neutral.
This chart is the result of the consolidation of the 25 biggest (and best) stories about hacking that have been published at IEEE Spectrum. They took both the good (those who hack to express themselves creatively without doing harm to others) and the bad (motivation: money, power, politics, and mischief), and of course, the ones that fall in between. They identified two parameters: innovation and impact. Using these parameters, they came up with this chart.
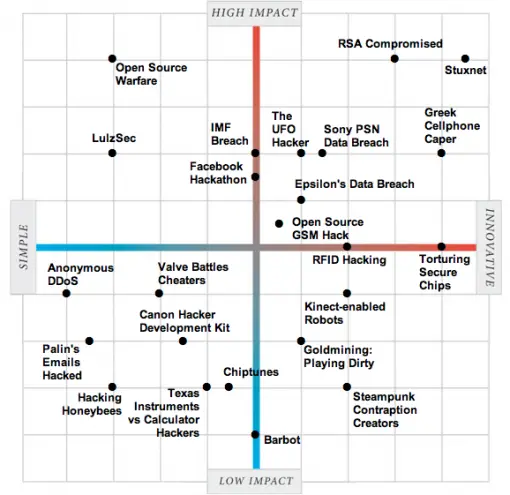
In the chart above, you can see the complete range of hacking activities covered by the site. In case you only want to do good, here is a simplified version, with only the good hacks displayed.
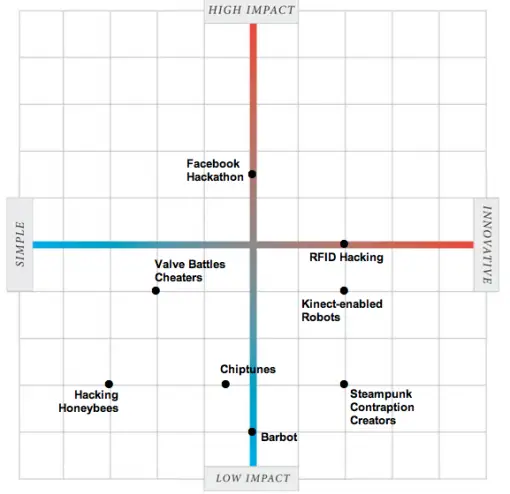
You can visit the site and play around with the options (even though there are only three). Now, you have to realize that the chart has been created by people with their own perspectives and opinions, so you might not necessarily agree with their assessment of the activities. In any case, you are totally free to let them know what you think about their assessment.
The bigger question is this: given that chart, where do you think your activities (if any) fall? Care to share?



