 How worried are you about your security when you go online? AVG, one of the most recognized names in anti-virus protection and Internet security in general, recently conducted a study on the state of online security in various countries. Involved in the study were 144 countries and 127 million systems. AVG collected data relating to virus and malware attacks on these computers and collated their findings.
How worried are you about your security when you go online? AVG, one of the most recognized names in anti-virus protection and Internet security in general, recently conducted a study on the state of online security in various countries. Involved in the study were 144 countries and 127 million systems. AVG collected data relating to virus and malware attacks on these computers and collated their findings.
The results?
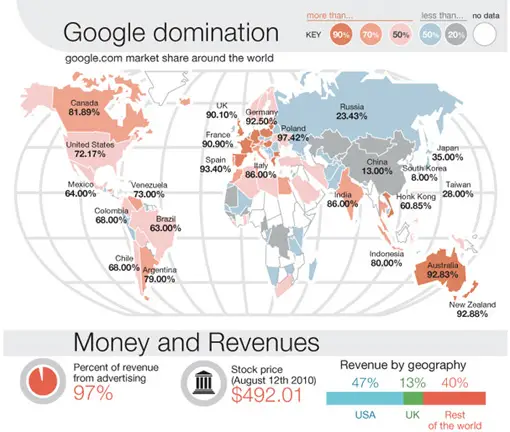
African countries did very well in the survey – seven of the 10 safest countries hail from the continent. Sierra Leone tops this list with an average of one attack per 692 users who surf the Web. Next in line is Niger, with one attack per 442 users who surf the Web. Other countries in the top 10 are Togo and Japan. Here are the details for each continent (attack per number of users)
- North America: 1 in 51
- Europe: 1 in 72
- Asia: 1 in 102
- Africa: 1 in 108
- South America: 1 in 164.
Basically, South America is the safest while North America is the most dangerous.
However, if the stats are broken down per country, the most dangerous countries are (first one being the most dangerous):
- Turkey (1 in 10)
- Russia (1 in 15)
- Armenia (1 in 24)
- Azerbaijan (1 in 39)
- Bangaladesh ( 1 in 41)
Roger Thompson from AVG is quick to point out, however, that this data does not exactly pinpoint which regions are completely safe from virus and malware attacks due to their nature – they are not really hindered by geographic boundaries. He also notes that the results of the study may not be applicable in the near future as viruses and attacks do change over time.
One interesting thing that Thompson mentioned is how this data can be of use to travelers:
However, our research should also serve as a warning to all travelling abroad and using the internet. If you are travelling without your computer and use a public machine or borrow a friend or colleagues, ensure that when accessing web -based services like email, that you log out and close the browser when you have finished your session and that you don’t agree to store any passwords or log-in information on that machine.
If you are taking your laptop with you ensure you have backed up your data and removed any sensitive information from your machine.
If you don’t want the hassle of worrying about security, just take a vacation in Sierra Leone. 😉
Photo credit: highwaycharlie