When TechCrunch published a post saying that they have obtained some vital Twitter documents from some hacker who got into personal accounts of some Twitter employees, the news spread like a wild fire in the forest. And as quickly as this news hit the headlines of most tech sites, Twitter also quickly replies and explains “vital information” regarding these so called vital documents. [Read more…] about Twitter Explains the Stolen Documents Issue
Security
Twitter Worm Attacks Continue
The worm that started wreaking havoc on Twitter last Saturday continues its attack. Already on its fourth attack, the new variation of the XSS continues to compromise Twitter accounts and post malicious tweets on Twitter users updates. [Read more…] about Twitter Worm Attacks Continue
Check if Your Gmail Account Has Been Hacked
If you rely on Gmail as much as I do, you probably worry about someone hacking into it right? Well, among the advanced features on Google’s mailing service there is a cool little trick that you can use to monitor “foreign” activity on your accounts.
The tip is coming from Make Use Of, and it is really easy to use.
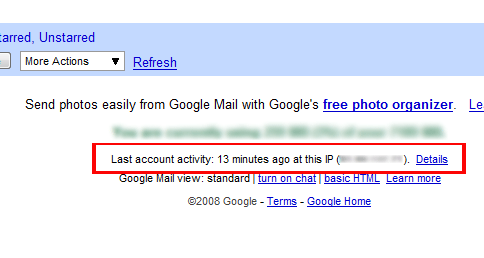
You basically just need to check the bottom of your Gmail account for the “Last activity…” message. There you will see when the last login was effectuated, and using which IP address. You can also click on “Details” to see a list of the last logins, their IP address, browser and so on. All you need to do, therefore, is to check if you are really the only person using your Gmail account!
Security Trends of 2008 Part 4: The Dreaded Storm and MPack
Picking up from the last time after my two-month long hiatus, I bring you now the greatest security threats of 2008: Storm and MPack.
Storm Blows Web 2.0 Away
The Storm malware is actually a collaboration of Web 2.0 techniques like social networking and dynamical associations towards a system. Simply put, it uses the most common web techniques in a two-stage attack, which we discuss later.
According to IronPort’s 2008 Internet Security Trends, Storm-class malware has its key characteristics:
Self-Propagating – sends massive amounts of spam to spread. Users are directed to multiple changing HTTP URLs, which serve Storm malware. If infected, the system then becomes part of the network.
Peer-to-Peer – where previous botnets were controlled from centralized locations through a hierarchical management structure, nodes communicate through a unique peer-to-peer communication protocol. This makes it difficult to track the total size.
Coordinated – Storm will send spam campaigns that point to webpages hosted by other computers, showing amazing sophistication in the way the network creates its attacks.
Reusable – can be used for many kinds of attacks: spam, phishing, DDoS, it has even been known to compromise IMnetworks and post blog spam, making it a threat to many different protocols.
Self-Defending – Storm watches for signs of reverse engineering or analysis. It repeatedly launched massive denial of services attacks against researchers and anti-spam organizations.
Through these, Storm was able to accomplish a huge number of PDF, XLS, MP3 spam outbreak over the course of 2007 and even up to today.
Storm Signaling: The Two Attack Stages
Storm uses e-mail functions and interconnectivity of Web 2.0 in order for its two-stage attack to take place. Also, Storm creators have come up with a “drive-by” browser exploit that infects computer simply through a web page visit, no downloads needed for infection!
Once a Storm malware infects a computer, it connects its victim computer into a peer-to-peer network, the Storm Network. This network is a modified design, decentralized and excessive, unlike its older, centralized ancestor. The creators seemingly acknowledged the fact that a centralized network is easy to destroy just by “chopping the botnet’s head off.”
Apart from the peer-to-peer feature, Storm also needs to maintain itself via self-defense measures. It utilizes Distributed Denial of Service to both prevent people from exploring the innards of a Storm malware, and launch a retaliatory attack to the onlookers.
Once the Storm network has possession of the victim system, it can instruct its victim to do either send a recruitment spam and aid in the network growth, serve malicious web pages, attack instant messengers, provide fast-flux and domain resolutions, or post blog spams on other websites. These actions can ensure that Storm will persist even if some of its victims are paralyzed, because it launches large-scale attacks that recruit other victims into its network.
Storm doesn’t actually attack head-on, as most of its deceased ancestors did. Unlike those suicidal malware, Storm-class malware seem to value its life, that it focuses more on its staying power than its destructive one. It is very frightening to know that while the Storm hasn’t completely been eradicated, its designers are improving it at a fast pace.
MPack: The Marketed Malware
MPack is actually a malware kit that is sold for anywhere between $700 and $1, 000. It is a PHP-based malware kit being sold by a certain group of Russian software developers known as the Dream Coders Team. In a CNET interview, Yuval Ben-Itzhak, chief technical officer of security company Finjan, stated how dangerous the Mpack kit is. “Without any computer science skill or any security background, you can install this package on any Web server and start to infect people with malicious code,” said Ben-Itzhak in the interview.
The commercial malware, as I would like to call MPack, is designed specifically for web-based attack, pretty much like Storm. It is deployed using an iFrame attack placed silently into legitimate websites, keeping infection and, interestingly enough, its attack statistics. Further, its creators, the Dream Coders Team, gives one-year support, fresh exploits (like the one Storm has), and add-ons that can cost anywhere from $50 to $300,possibly based on attack modifications.
While having these kind of malicious kits in the market is not that new, support services do seem to be appealing, especially for a novice who wants instant ability over malware infection.
MPack Attacks!
MPack kit owners are provided with an administrative interface to launch their attacks, usually by the same drive-by exploits utilized by Storm. Further, the interface keeps the statistics on both viewers of an infected web page and the successful attacks it carried on. It somehow gives satisfaction to the user for purchasing the malware kit, not to mention the support services and “additional arsenal” that can make a novice a force to reckon with.
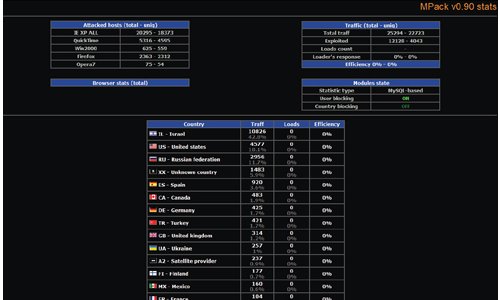
Storm and MPack malware have been spreading like wildfire since mid-2007 that it has become very alarming. The things most feared about the two are their peer-to-peer and self-defense mechanisms that allow the malware to creep into a network and destroy it from within. Also, considering that the protocol used by both Storm and MPack is HTTP, it’s really hard to recognize a social malware from a safe web page. Without a plug to pull or a switch to turn it off, it has come to attention that these malware can be considered professional in a sense – there are experts behind the longevity of these malicious software. The question that arises now would be: How can we avoid being attacked by these malware?
For Safety And Precaution
Increased sophistication. That phrase summarizes the greatest threats of 2008, although conventionally, malicious programs still do what they do best: advertise, infect, steal data, and spread. In their line of evolution, developers learned that a one-step approach is no longer plausible, and the improved two-step route they are taking is more than anyone can handle.
With a new way to launch attacks while ensuring a defensive mechanism for themselves, Storm- and MPack-like malware are hard to deal with. They easily render previous security measures obsolete. In order to protect your system from those malware, new ways are being preached and practiced. IronPort’s 2008 report summarizes these safety measures into five:
1. Secure web traffic. The reputation of a website is a key to determine how plausible a malware can infect it. Let’s have Yahoo for example. It’s reputation as legitimate and virus-free makes it hard for user-generated malware to penetrate it.
2. Deploy preventive protection for e-mail. The alarm brought about by Storm- and MPack-class malware calls for multi-level spam defenses, commonly available in our favorite e-mail service providers. Deploying these defenses can easily detect and separate possible malware attachments.
3. Protect against corporate data loss. Commonly, attacks from malware scans your hard drive to collect private information. It wouldn’t hard a company if it would require its employees to scan outgoing transfers and connections for possible policy violations. It would show how cautious your company is and give it a reputation for safety, adding to its market level.
4. Prevent “phone-home” activity. It is very important to scan or totally block outgoing “phone home” activities, as the sender might be malware-infected, retrieving attack commands or uploading data back to operators.
5. Track important communications. New technologies are available for real-time tracking of your e-mail messages, which works similar to physical package shipping. Added care wouldn’t hurt to our noble and easily accessible e-mail accounts, as they have become an integral part of our virtual lives, while others keep on attacking us through them.
Malware sure has spread everywhere on the Internet, but we should still be the masters of our own virtual spaces. I hope this four-part series will aid you through the rest of 2008! Happy surfing!
What is Phishing? An Introduction

The Internet is a vast world, so vast that it somehow is an existence similar to our real world: IP addresses for home addresses, e-mails for snail mails, even calling-enabled messengers for telephones and mobile phones. But a world is not a complete world without its prevailing crimes, right? If so, which crime is as widespread in the Internet as robbery is to the real world? It’s phishing.
Phishing is an act of illegally acquiring sensitive information, like usernames and passwords, from an unsuspecting user. Like fishing, the word it originated from where you use worms as bait to catch fishes, of course, phishing uses trustworthy websites (usually the online transaction types like e-bay and PayPal), e-mails, and online messengers for bait to catch unaware users and get sensitive information from them. But unlike computer viruses, which attack the computer’s internals, phishing deals a more serious damage in a personal, commonly financial level.
There are numerous ways for malicious Internet connoisseurs to phish out sensitive information. People who depend on Internet-based transactions should be wary of these phishing techniques that we will discuss next.
Link Manipulation
The most common of all phishing techniques in existence is link manipulation which, as the name states, directs your browser to a website different from the original website you are to visit through fiddled links. Link manipulation usually comes in the form of an e-mail message from what you think is your trustworthy website. Let’s look at a scenario that shows how link manipulation works.
You are checking your e-mail account when suddenly you receive a notice telling you to protect your PayPal account. As you click on the e-mail message link, you read through a seemingly original PayPal message, telling you that PayPal administrators have “noticed” that you attempted to log in using a foreign IP address (a clever alibi, I must say). In the middle of the baffling message appears a highlighted sentence telling you to verify your account, followed by the manipulated link. And after that, a frightening message appears: “If you choose to ignore our request, you leave us no choice but to temporarily suspend your account.” That really leaves you no choice but to follow their manipulated link. Since you cannot afford to temporarily lose access to your virtual bank account, you clicked on the link, which opened the website created by the phisher. On the webpage, you are asked to enter your username and password to “log in” to your account. Thinking that you are furthering the security of your PayPal account, you provided the username and password, et voila! The phisher now knows your username and password and can eventually use them for his gain!
Often, such spoof websites have very minute differences from the original so the link can go unnoticed from a careless eye. Phishers use subdomains in order for their spoof link to keep a reference to the spoofed website, without really connecting to it. Also, phishers trick their victims by using deceiving anchor texts, words or phrases that stand for a link in a website. Through it, the spoof website looks legitimate since the anchor texts act as cover for the phishing link. And on a more complicated note, phishers can also use redirectors of Uniform Resource Locators or URLs to hide their phishing links behind trustworthy websites and domains.
What if you installed an anti-phishing filter to detect phony text contents of e-mail messages and web pages? Think you are safe enough? Think again. Phishers have seen through this, and their methods evolved from phony, plain text messages sent via e-mail providers. Filter evasion methods include using other web objects like images to avoid their manipulated links from being detected by filters.
Website Forgery
Phishers can also use fake web pages to phish out information. This method is known as website forgery, which comes in two devilishly wise packages.
The first method of website forgery uses scripting methods to conceal the manipulated link in the web page’s address bar. Commonly, phishers imitate the address bar logos of trustworthy websites and put them beside URLs of their deceiving website. Further, the phisher’s scripts can even close the address bar containing the phisher’s link, replacing it with an address bar containing the genuine URL to obscure the website’s identity.
The second method of website forgery is done through exploitation of a website’s flaws. Cross-site scripting or XSS uses a website’s programming defects to trick an unsuspecting visitor. XSS is a very convincing phishing technique, because what it does is open the authentic website wherein the victim fills up forms for usernames, passwords, and other confidential information. But upon submitting the page, XSS scripts start working, linking you, the persuaded victim, away from the authentic website and into the phisher’s own. Sometimes, the phisher wouldn’t even need their own websites, for their script is enough for the deception to occur. Such phishing attack is difficult to detect just by merely “looking around” the website. Without prior knowledge on scripting and the like, you will never know what hit you, or in this case, you’ll never notice that you got robbed virtually.
This case is turned from bad to worse by the fact that there exist phishing kits, programs with user interfaces that allow reproduction of websites and creation of their fake versions. Such kits are often used by script kiddies—malicious but amateur programmers who cannot develop their own set of wicked programs, using programs that other malicious programmers like hackers developed. Man-in-the-Middle is one example of phishing kits that enables despicable pseudo businessmen to “mediate” between legitimate online businesses and their clients. Man-in-the-Middle channels information from a business website to a fraudulent website and vice versa in order for the amateur phishers behind the crime to communicate with their victims. Through this, the crime perpetrator can easily capture the victim’s confidential information in real-time setting. This technique spreads phishing to the not-so-knowledgeable script kiddies to build a growing network of virtual criminals. Also, the kit was so flexible that it can be customized based on what type of online business the script kiddie criminal wants to target. Further, the fake website can easily interfere through the transactions between the original website and the victim by “importing” from the target website the victim’s sent information, meaning all credentials of the victim can be viewed and acquired by the phisher. Fortunately, the said phishing kit was discovered by the anti-fraud division of an American software and systems manufacturer.
Other Techniques
Internet frauds don’t only involve websites. When you receive an e-mail message telling you to dial a certain number, doubt it immediately (unless you are expecting some transactions from the website, of course). This might be a voice phishing attack. If you dial the number provided by the phisher in the e-mail message, voice prompts will be asking you to press numeric information about your bank account like your account and PIN number. Phishers have arrays of faking techniques to employ to fool users. They can use fake caller ids to give the call a legitimate, trustworthy feel, an IP service that provides voice-overs to communicate with you in real-time setting, and even access on information keyed through a landline phone.
Although there are anti-phishing toolbars that check websites if they are one of the identified spoof websites in an Internet-wide database, phishers have found a way to further conceal their identity from anti-phishing programs which evolved from mere filter evasion. Introducing: the phlashing technique.
Confident that the anti-phishing programs are the ultimate salvation from phishers, users get that false security feeling that they are protected from any kind of phishing attack. Sadly, phishers were able to think outside the box (or the four corners of the webpage window) and learned to use Macromedia Flash animations as means to create their spoof websites. Such knowledge, in essence, defeats the purpose of anti-phishing services “with the phisher’s hands tied behind his back.” Since anti-phishing programs scan only the text contents of a suspicious website, phlashes can just pass the anti-phishers with flying colors.
As the phishing activities evolved, cyber criminals developed their wicked craft even more, anticipating possible reactions from the security militia of the Internet. Phishers even entered the world of compressed files to easily spread chaos among networks of banks and online transactions. Developing a somewhat plug-and-play phishing network using zipped files on hacked networks, web cons enjoy a phishing spree just by unzipping certain files in a subdirectory of an exploited website. Falsely becoming part of the target website, the unzipped spoof files inside the website’s subdirectories will look just as legit as the directories above it.
Social Network Phishing
Although this only comprises a small percentage of phishing activities, social network phishing is just as grave as its ancestors in the sense that it attacks major groups of web users at once through online community websites. In here, a phisher targets a certain social network like MySpace or LiveJournal, planting in those websites some botnets, automatic and autonomous programs run remotely by a hacker. Although there isn’t much money involved in social networks, phishers still consider them their pot of gold as it is very easy for them to spread key loggers, programs that can capture every keystroke of the user. Phishers use such networks in order to hopefully capture a home computer that is often used to shop online or store money via online banks. Further, most of the people in social networks use the same password for any and almost every account they have in the Internet universe, including their e-mail addresses where most confirmation messages for online transactions are stored. That and the fact that key loggers can acquire passwords are enough warnings for amateur people who use the web for transactions. Other typical social networks that phishers target are bulletins, forums, commentary, and profile websites.
There is another form of phishing that attacks big groups instead of just a single person, and that technique is known as spear phishing. In terms of attack deployment, spear phishing somehow resembles the exact opposite of social network phishing because the former uses somebody from the organization to set up the attack, as compared to the latter, which uses a community website to attack individual users.
Spear phishers actually need three things in order to execute an attack to an organization: (1) an identity of somebody within the organization, preferably a person with high authority to make the attack convincing, (2) wide knowledge about the company’s transactions and daily activities to back up the validity of the phish, and (3) a seemingly valid and well-researched reason for requesting confidential data like the PayPal account of one of the company’s departments. If these three are already available to the phisher, then the spear phishing comes to actuality, as described below.
In spear phishing, after finding a website suitable for the attack, the phisher acts as if he is a member of the website’s company with a position of authority. This step utilizes the first of the three requirements to conceal his identity and at the same time, be more convincing when he would be sending requests for confidential information. However, before he creates the fraud e-mails, he has to first look for traces of financial and confidential information, which he can use to further infiltrate the company, supporting the validity of his next move. In that step, he utilizes the second requirement. And lastly, the crime perpetrator then drafts the e-mail message directed to the company, using as reason the third requirement, in order for the phishing to take place.
The typical information that the spear phisher requests in his fraud e-mail message are the same as any kind of phisher would ask: usernames, passwords, account numbers, and the like. But furthering the attack, the spear phisher provides a manipulated link that, once clicked, will download a malicious program into the computer of the victim.
Phishing is as varied as robbing is in the real world. And with the many techniques above, with some even requiring phishers to study and improve the technique, I can’t help but wonder what the driving force for a phisher to phish is. Let’s explore a phisher’s mind in the next section.
A Net Full of Phishes
Everyday, an average of 10 phishing attacks are developed to dupe varying online transactions. However, in this constant increase, the concern of people is more directed to stopping phishers by putting up layers and layers of phishing security programs. Fortunately, I am one of the few people who have heard of the saying: “Prevention is better than cure;” so I decided to learn what goes on inside a phisher’s mind. Upon researching on phishing and trying to figure out how a phisher’s mind thinks, I stumbled upon a website wherein an article they published discussed how it is to be a phisher.
In the earlier years of phishing, a phisher is known to be someone who experienced being phished or had witnessed somebody suffering from the damages of phishing at one point in his earlier life. Given that he or she had ample background of the Internet and its programming styles, then that person can imitate the phishing attack that got him or somebody close to him to do revenge or simply to acquire personal, financial information. But with the dawn of phishing kits, almost anyone can do it, like the novice script kiddies mentioned above.
In the course of a normal phisher’s life, he or she “gains” a multitude of virtual identities, acquired using the techniques we discussed above. Often, they can no longer track all those whom they have phished that they start building databases of phished credentials from their victims.
Phishers don’t stop when they have acquired some identities. Even though they are getting enough money from a good number of victims, phishers still are insatiable that they started resorting to social phishing. Usually, social networks contain e-mail addresses, which are accessed by the phisher once he gets hold of his victims’ passwords through key loggers. Upon looking around the e-mail addresses of his victims, the phisher can then determine how much his gains will be.At times, when the victim is registered to online transaction websites like eBay and Paypal, the phisher sells the accounts to scammers, who will be the ones doing the stealing.
When they start phishing, phishers become very meticulous virtual entities as they try to select the best Internet services to handle their attack elements: a convincing domain and an anonymous, often offshore host to carry out their spoof websites and Internet files and connections. Second, the phisher checks the page source of his target website, studying it to identify where he can place certain codes that will do the phishing for him. Third, he develops the spoof website with care and keenness so as to make it believable. After that, he will include certain scripts that will transfer information from the spoof page to his server using scripting languages for backend of websites. Lastly, he will deploy the spoof web page using any or all the techniques shown above, and wait for the “phished to take their bait.”
Phishers can fool as much as 10,000 people everyday. But to remain hidden from such big crowd, a phisher has to use his own virtual private network, a personally dedicated server, a copious amount of proxies, and encryption of his network signals that travels to and fro.
Finally, the reason why a phisher can still catch a good haul these days is because their adversaries, the good guys of Internet security, are “lazy” that phishers maintain a firm step ahead of them.
That’s pretty much it for the first part of our expedition in the world of phishing. In the second part, we will learn how to stop or avoid malicious phishing activities. Stay tuned!
Modern-Day Security Your Business Absolutely Needs
It’s imperative that you secure all of the aspects of your business. You have to secure any proprietary data. You have to secure your IT network. You have to secure your financial information. But not everyone is a specialist when it comes to security. You may be running on autopilot when it comes to setting up your information structuring, and you may not realize what kind of risks are out there. That’s why it’s so important to research this matter and create solutions before you have problems. [Read more…] about Modern-Day Security Your Business Absolutely Needs