 Tech-savvy individuals would know all about geotags. Initially, the whole idea can make you overly excited. When you hear about what happened to Adam Savage (of Mythbusters fame), though, you might think twice about enabling thing function.
Tech-savvy individuals would know all about geotags. Initially, the whole idea can make you overly excited. When you hear about what happened to Adam Savage (of Mythbusters fame), though, you might think twice about enabling thing function.
Basically, geotagging allows data to be embedded in different media such as photos and videos. For example, when you use your iPhone to take a picture, the longitude and latitude can be included in the file. When uploaded to a web site, anyone who views the file can extract that data.
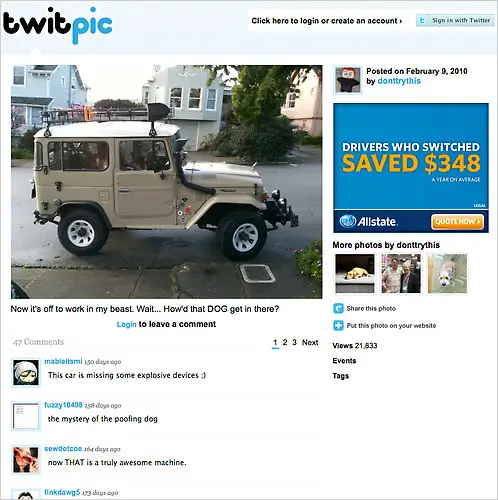
That’s what happened to Adam Savage, who posted a photo of his ride to work on Twitter. As a caption, he wrote “Now it’s off to work in my beast. Wait…How’d that DOG get in there?”
Nothing’s wrong with that, right? Think again. The photo included details on the exact location of his home (where it was taken). His caption also revealed the information that the house might be empty in the next several hours. You see where I am going with this?
You’d think that someone like Adam Savage would have known better than to do something like this, but he salvaged the situation quite well by saying that he was not at all concerned about the issue as he is not famous enough to be stalked. Now I am not so sure about that…Oh, and yeah, he moved to another house.
Anyhow, even if you are not a public figure like Adam Savage, you might want to disable that geotag function. After all, you know how ingenious unscrupulous individuals can get.
Photo from The New York Times